Sustainability | GovernanceInformation Security
Our Approach
Governance
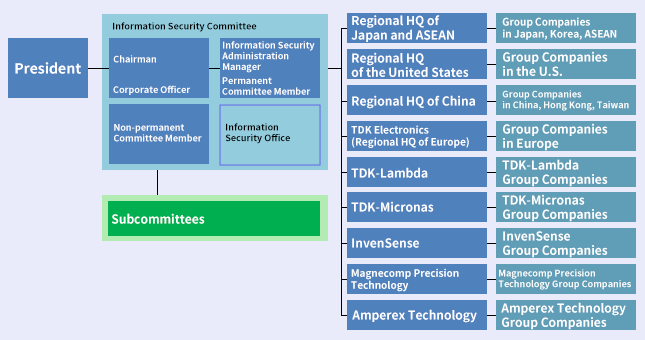
TDK has set up the Information Security Committee under the Executive Committee to adopt measures in response to information security risks in the Group as a whole. The Information Security Committee is chaired by a corporate officer and reports to the Representative Director, President and CEO once every quarter and to the Audit & Supervisory Board members twice a year.
In addition, to strengthen its information security governance, TDK has put in place a system whereby representatives of both head office functions and regional headquarters can be asked to serve as non-permanent members of the Information Security Committee, thereby enabling it to respond flexibly depending on the issue being addressed.
TDK requests the appointment of an information security administration manager in each company and operates a system by which a report is submitted to the Information Security Committee whenever, for example, an information security incident occurs or a team member (employee) notices something suspicious. In addition, based on the above governance setup, we stipulate the reporting route in response to the level of seriousness and emergency of an incident. In the case of a serious incident occurring or being detected, the Information Security Committee would respond swiftly in conjunction with the Crisis Management Committee.
Information Security Education
To maintain and enhance information security within the TDK Group, we implement information security education and e-mail security training for our team members.
The entire TDK Group keeps to enhance the education and training to team members by such as reflecting the latest security trends so that we will respond to risks that cannot be covered by the system.
Strategy
Since such occurrences as the stoppage of production, sales, marketing, R&D, and other activities due to cyberattacks and the loss of trust and reliability due to the leakage of information have a serious business impact, TDK considers information security to be an important management issue.
To prevent the occurrence of damage and to minimize damage in the event of an incident, TDK is strengthening information security measures based on the Cybersecurity Framework of the US National Institute of Standards and Technology (NIST) ((1) govern, (2) identify, (3) protect, (4) detect, (5) respond, (6) recover).
[Principal Measures]
-
Building of TDK Zero Trust ((2) identify, (3) protect, (4) detect)
To prevent the occurrence of damage and to minimize damage in the event of an incident, we will undertake the building of TDK Zero Trust.
Zero Trust means constantly restricting and monitoring access to all users, devices, and networks, thus preventing attacks from outside and controlling internal proliferation. We will build TDK Zero Trust in a manner appropriate to TDK’s business environment. -
Supply-chain security ((1) govern)
To prevent TDK’s business activities from coming to a halt, we are monitoring the state of information security and making improvements not only at TDK but at all TDK Group companies. -
Measures to counter the risk of internal irregularities ((3) protect, (4) detect, (5) respond)
To prevent the loss of trust and reliability due to the leakage of information, we will prevent internal irregularities by using AI monitoring tools, etc. -
Incident response ((5) respond, (6) recover)
We have established the Computer Security Incident Response Team (CSIRT) as an organization to respond to information security incidents in a manner that minimizes damage and enables speedy recovery, and we have stipulated our response setup and response plan should an information security incident occur in the Computer Security Incident Response Plan (CSIRP).
Risk Management
The Information Security Committee conducts surveys of the latest security trends, and reports on the results to senior management. With regard to risks that are of significant concern, we verify the status of risk countermeasures within the TDK Group, and in the case of risks that require additional response measures, we formulate appropriate measures and then roll them out throughout the TDK Group.
We also liaise with the Enterprise Risk Management (ERM) Committee in regard to enterprise-level risks.
As regards external risks, we are constantly evaluating risks from the perspective of hackers who might launch cyber-attacks, and from the perspective of the Internet. In the case of high-risk vulnerabilities that need addressing, we take action promptly.
We make use of a website protection service to block external attacks on our website.
With regard to internal risks, we are implementing countermeasures to prevent team members from disclosing information outside the company without authorization.
Metrics and Targets
Medium- to Long-Term Targets
-
TDK Zero Trust
To prevent the occurrence of damage and to minimize damage in the event of an incident, we will undertake the building of TDK Zero Trust. Zero Trust means constantly restricting and monitoring access to all users, devices, and networks, thus preventing attacks from outside and controlling internal proliferation. We will build TDK Zero Trust in a manner appropriate to TDK’s business environment. -
Assessment of vulnerabilities by an external disclosure environment evaluation system
800 or more points out of a total of 950 points for all assessed systems (Grade A)
FY March 2027: Achieve goals by the final year of the Medium-term Plan.
Goals and Achievements in FY March 2025
| FY March 2025 Goals | Achievements |
|---|---|
| Define TDK Zero Trust, and set goals to be achieved during the period of the current Medium-term Plan | Defined TDK Zero Trust, set goals to be achieved, and promoted activities for achieving the goals |
|
Assessment of vulnerabilities by an external disclosure environment evaluation system : 800 or more points out of a total of 950 points for all assessed systems (Grade A) |
Achieved 800 or more points (Grade A) for all assessed systems. |
[Main Achievements]
TDK strengthened information security measures in accordance with the NIST Cybersecurity Framework.
- We evaluated vulnerabilities in all TDK Group companies as seen from the Internet (using an external disclosure environment evaluation system) and identified and improved vulnerabilities ((2) identify, (3) protect, (4) detect).
- We checked the state of information security in our supply chain and supported improvements; we also expanded the scope of related activities undertaken within the TDK Group ((1) govern).
- We continue to conduct training on information security incidents (for management and overseas business sites, etc.) ((5) respond, (6) recover).
- As a measure to counter the risk of internal irregularities, we introduced AI monitoring tools to our overseas business sites and strengthened our measures to prevent internal irregularities ((3) protect, (4) detect, (5) respond).
- We implemented information security education and email training ((3) protect).
Evaluations and Future Activities
In FY March 2025, which was the first year of implementation for building TDK Zero Trust, we clarified the definition of TDK Zero Trust throughout the TDK Group, and formulated the plan for realizing it.
In this fiscal year, we built the necessary framework through collaboration between TDK Group companies, and promoted related activities.
We aim to achieve the goals that were set in FY March 2025 for the final year of implementation of the Medium-term Plan by FY March 2027.
Initiatives
[Initiatives to Strengthen Information Security]
-
Building TDK Zero Trust
In FY March 2025, we defined TDK Zero Trust, set goals for its realization, and promoted activities directed at the achievement of these goals. -
Supply-chain security
To prevent interruption to TDK’s business activities, we have been rolling out the following measures across all TDK Group companies, proceeding with the clarification of information security status not only in TDK but also in the supply chain, and making improvements where needed.
In light of the latest changes in the information security environment, we have expanded the scope of our activities.- Using questionnaire surveys to verify the state of the information security management system and the rules governing its operation
- Using an external disclosure environment evaluation system to determine vulnerabilities
- Using individual surveys to verify actual operational status
-
Strategies to Address Risks Relating to Internal Irregularities
To prevent the loss of trust and confidence due to the leaking of information, we have expanded the adoption of AI monitoring tools to include overseas business sites, and we have been implementing various measures to counter risks relating to internal irregularities. -
Incident Response
We implemented incident response training for senior management, clarifying the role that senior management are expected to play, and how they should respond.
For frontline personnel who will actually be implementing the response to incidents, we implemented incident response training at our business locations in Japan and overseas, and we clarified the procedures that should be followed when an incident occurrs.
[Introduction of TDK’s Declaration of Partnership Building initiatives]
TDK’s initiatives relating to supply-chain security were introduced in the case list of Declaration of Partnership Building efforts compiled by Japan’s Small and Medium Enterprise Agency:
Information Security Education
To maintain and enhance information security throughout the entire TDK Group, we implement information security education and training in dealing with targeted e-mail attacks for all team members at least once a year.
Information security education is implemented for computer users at each Group business site. The content and frequency of the education is tailored to suit the environment and current status of each site.
With the e-mail training, an e-mail modeled on a real phishing e-mail is sent to each team member, to verify the number of team members who open the attachment or click on the URL.
Identification and improvement of vulnerabilities
We carry out constant and global monitoring from the Internet side from the perspective of hackers launching cyberattacks and swiftly take action in the case of risks of high vulnerability requiring countermeasures. Furthermore, one or more times a year we implement third-party vulnerability diagnosis in the TDK Group so as to identify and improve vulnerabilities in the management of information security.
Strengthening of response to security incidents
We have established the Computer Security Incident Response Team (CSIRT) as an organization to respond to information security incidents and have stipulated our response setup and response plan should an information security incident occur in the Computer Security Incident Response Plan (CSIRP).
The TDK Group has formulated a Business Continuity Plan Relating to Information Security (IT-BCP) and stipulates in advance how to respond in the case of an information security incident arising. In addition, we implement IT-BCP training one or more times a year and, in light of the results, regularly review the plan.
External Certification of Information Security Management
A number of TDK Group business sites have been awarded Trusted Information Security Assessment Exchange (TISAX) information security certification, which was initiated by the German Association of the Automotive Industry (VDA).
Related Information
Protection of personal data
Based on the TDK Privacy Policy, TDK endeavors to protect personal data and privacy. In addition, we stipulate the TDK Personal Data Protection Basic Policy as part of the TDK Privacy Policy, which is applicable to all personal data handled by TDK.
Related link
The TDK Group considers personal data also to be one aspect of information security, and we endeavor to properly manage personal data through our information security setup. We check the state of personal data management annually and make corrections and improvements in accordance with the results.
We have established the Personal Data Protection Subcommittee under the Information Security Committee. This subcommittee, which has been designated as the body in charge of protecting personal data, serves as the contact for inquiries related to the handling of personal data.
Filing of Complaints Regarding Privacy Violations
In FY March 2025 there were no reports or receipt of complaints in Group companies concerning the infringement of customer privacy or the loss of customer data. There were also no instances of using customer data for secondary purposes.